INTRODUCCIÓN
The current stage of social development can be characterized by the increasing influence of information sphere, which includes not only the information itself, but also information infrastructure and entities that collect, store, distribute and use information. Therefore, one of the spheres of social life, in which the role of the State has not been sufficiently studied, is the information sphere.
The need to regulate the information sphere determines the need for an appropriate direction of the State's activity - the State’s information function.
The implementation of the State's information function on the internal level is aimed at optimizing and improving the efficiency of public authorities work. Most often it includes optimization of processes that contain information with limited access or information that cannot be disclosed due to the internal belief of public authorities that there is no need to make it public, and there is no direct regulatory requirement for its disclosure.
At the same time, the creation of a full-fledged state information system is impossible without creation of a unified architecture of state structures, which simplifies the process of interdepartmental cooperation. The informatization in this sphere is aimed at improving the mechanism of information exchange between various parts of the State’s management system, developing measures to optimize internal information systems, and eliminating intra- and interdepartmental barriers.
Cloud computing is now becoming one of the most common IT technologies for deploying applications due to its key features: flexible solutions, on-demand availability and good price/quality ratio (Werner, 2012).
At the same time, the most critical issues in building a cloud-based infrastructure involve information security aspects. Achieving an organization's information security objectives is a key factor in decision-making on IT outsourcing services and, in particular, state administration bodies’ data asset migration to different models of cloud services providers. Therefore, when moving to a new model of IT services provision, special attention should be paid to the issues of ensuring data processing security (Berdnik, 2013).
The analysis of possible threats and risk analysis are the basis for the choice of measures to provide information security of cloud computing systems, which must be executed to decrease risk to accessible level (Werner, 2013, Radin, Zubarev, 2014).
While a quantitative risk assessment is widespread in some spheres such as finances and credit, a quantitative risk assessment in information security is usually accompanied by a row of restrictions where the absence of data for verification of these methods takes a special part (Kachko, Lavrynenko, Tsaregorodtsev, 2014).
Suggested approach for risk analysis and management will allow to make reasonable decisions when choosing information security systems, software for components of information systems (IS), functioning on a basis of cloud computing technologies.
MÉTODOS O METODOLOGÍA COMPUTACIONAL
The method of building an information security system on cloud architecture
Today, a number of open information security issues do not allow building secure cloud services for critical assets processing. It is only by including demilitarized zones (DMZ) as a private cloud into the architecture that we can provide the required level of security for processed data.
The private cloud environment (PCE) is characterized by the advantages of a traditional (internal) IT infrastructure, namely: the ability to apply best practices, methods and metrics for risk analysis and assessment, full control of every central IS management process and the ability to conduct internal audits. The main issues are serious financial costs of PCE creation and operation, limited scalability and fault tolerance. In addition to all the threats specific to the public environment they may also include errors in the strategic planning of the use of a computing capacity, which can reduce the availability, integrity and security of the data being processed.
The DMZ inclusion in cloud architecture is necessary to ensure an organization’s full control over its critical assets even in the face of high financial costs of PCE operation. Public cloud is needed to provide the required level of scalability and flexibility in allocating on-demand resources at peak system loads.
Use of components with different security levels leads to a new, hybrid type of cloud deployment.
To solve the problem of building a secure cloud infrastructure, we propose to consider the method of building a secure hybrid cloud environment (SHCE). The method will ensure compliance with security requirements, determine the sequence of critical data processing and ensure the location of this data between protected components of the cloud environment. Based on the above key stages of information security analysis of cloud infrastructure, we will describe the method in the Event-Driven Process Chain (EPC) notation.
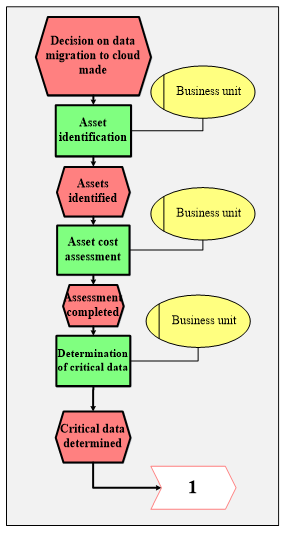
Stage 1 "Identifying and Assessing an Organization’s Critical Assets"
An employee of a business unit identifies information assets involved in the business processes to be automated within the cloud environment.
The employee of the business unit analyzes and describes in detail the organization’s business process by mandatorily indicating the functions responsible for critical data processing. In building and selecting a cloud architecture one should take into account information related to possible financial losses that the organization may incur in case of an unauthorized access to its confidential information. Figure 1
Stage 2 “Identification of Security Requirements and Determination of Data Processing Sequence in SHCE”
The IS service officer identifies information security requirements of the IT system based on cloud computing technology. One of the approaches to building an organization’s IS objective trees of the cloud infrastructure is considered in the paper (Tsaregorodtsev, Kachko, 2011) . The criteria and mathematical apparatus for "measuring" the system properties on objective trees based on such algebraic objects as semi-groups with a unit - monoids, is discussed in detail in (Kachko, Lavrynenko, Tsaregorodtsev, 2014).
The sequence of critical data processing based on the formalized security model of data processing in the cloud-computing environment is described in detail in (Tsaregorodtsev, Zelenina, Ruzicky, 2017). Figure 2
Stage 3 “Threat Identification and SHCE Risk Model Construction”
Information risk management is a key process of measuring various information security indicators. On this stage for each information asset, it is necessary to determine the level of its vulnerability, presence of potential threats capable of exploiting these vulnerabilities and to assess the impact of security incidents on the organization’s business processes in its daily operation. To succeed in implementing all actions of the risk analysis process, it is required to introduce control and countermeasure processes into the organization. Figure 3
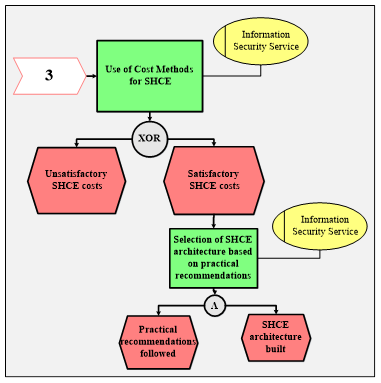
Stage 4 “Application of Cost Methodology and Construction of SHCE Architecture”
Using the cost methodology, the IS service officer obtains the costs of various options for SHCE deployment and, based on practical recommendations, selects various options for building SHCE architecture. Figure 4
Fundamentals of quantitative risk assessment method
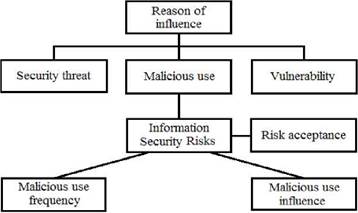
Let us define key concepts, which will be used in the suggested approach. The vulnerability is a software defect or a weakness in the security system, which can be exploited by third parties to cause damage or harm to an organization (Mell, Tim, 2011). Known vulnerabilities are vulnerabilities, which either have no bug fixes or have bug fixes, applied with a time delay. The security threat is a potential objectionable event in the object of assessment, which can lead to a successful use of exploit with unwanted influence on confidentiality, integrity and availability of assessment object assets. The result of vulnerability exploitation by any threat can be appearance of an unwanted event, which is called the malicious use (Accorsi, Wonnemann, 2010). It is worth to be noticed that malicious uses can appear only with the existence of threat as well as of vulnerability and concerned vulnerability can be exploited by a certain threat. It means that a multiplicity of all potential malicious uses is the subset of both vulnerability list and potential threats list. Consequently, where M - malicious events list, ST - threats multiplicity, SV - vulnerability multiplicity.
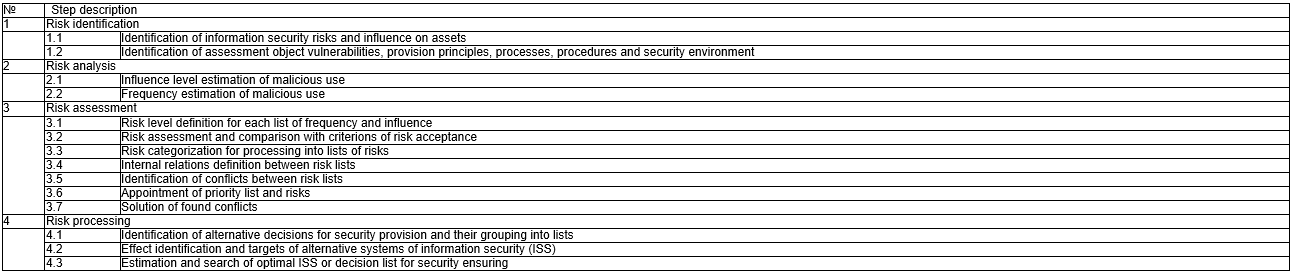
Let us present the qualitative risk assessment method in the form of the following steps (table 1).
On the top level suggested approach to risk estimation includes two general steps. First step describes an analysis managed by risk which includes malicious use list and connected with it risk levels estimation, which are the result of steps 2, 3 of suggested method with the following comparison of received data with criteria of risk acceptance which are defined at the first step. The result of this phase is a list of risks requiring processing (Tsaregorodtsev, Kachko, 2012).
Processing risk list, alternative decision list and other compromise parameters appropriate to the development, project or financial condition are the input data for the second step of the method, in frames of which information security risks are problems and challenges requiring decision in the form of available alternative security mechanisms (Tsaregorodtsev, 2013).
Described under the first step actions include key analysis elements: threat list, vulnerabilities, malicious use, its frequency and influence, information security risk, risk acceptance criterion (Winkler, 2016). Figure 5 describes key essences and their relations of the first step of risk assessment approach. All these constituents are necessary for evaluation of estimation object risk level and its assessment focusing on comprehension of what risk requires processing (Tsaregorodtsev, 2017).
Herewith a risk is calculated for every malicious use by means of combination of its frequency with one of influences. It means that malicious use leads to appearance of one or many information security risks depending on amount of interconnected factors (frequency and influence). Both indexes (frequency and influence) can be defined with quantitative estimation metric basing on data from public sources, one of which is NVD Common Vulnerability Scoring System Support (CVSS).
The frequency of malicious use and its influence can be presented in the form of quantitative indexes: certain number of appearances during time interval or possibility of malicious use appearance in certain time period. The influence can be presented in the form of financial reputation losses (Tsaregorodtsev, Kachko, 2011, Tsaregorodtsev, Kachko, 2012).
RESULTADOS Y DISCUSIÓN
Definition of malicious use frequency and corresponding influence on the basis of CVSS
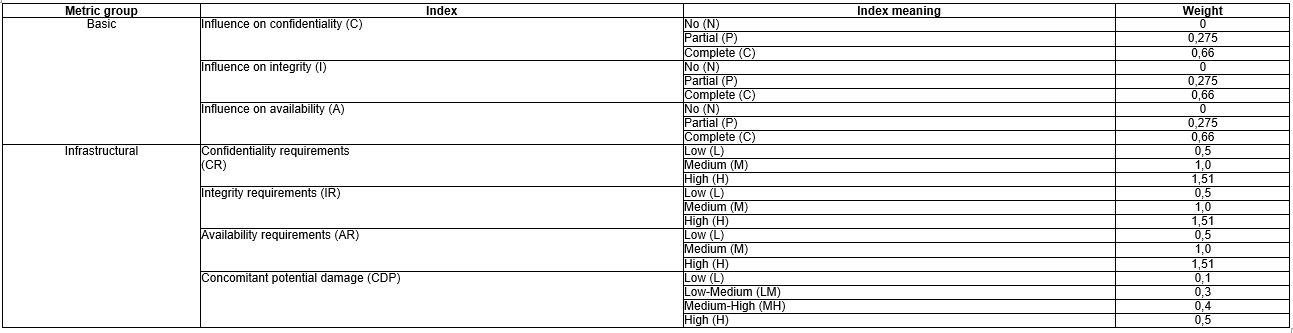
We use general prepositions of CVSS method for definition of two key variables influencing on risk estimation. For this purpose let’s combine indexes of basic, temporary and infrastructural metrics in a special way. The higher level of vulnerability to exploit use the more chances an attacker has to provide a successful attack and the higher is the index of malicious use frequency (F). Let us calculate this index for every vulnerability presented in the risk model of a cloud environment with assumption that fundamental vulnerability characteristics are described by the basic metric, and an index accounting of temporary metric will allow to decrease the probability of successful exploit use. The same principle is referred to the damage (influence): potential damage depends on confidentiality, availability and integrity requirements defined in infrastructural metric.
Table 2 and Table 3 describe indexes chosen for analysis with corresponding CVSS weights.
Using of three basic metric indexes and three temporary metric indexes allows evaluating malicious use frequency (how often vulnerability is the subject to exploit influence). Basic metric describes vulnerability characteristics and its liability to exploit influence because these indexes are chosen for determination of primary frequency.
It is considered that the primary frequency can be updated. Temporary metric indexes include indirect factors of vulnerability in question.
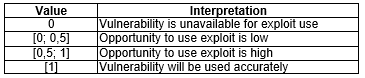
Then received estimation must be normalized to receive values within interval [0; 1], what allow interpretation of received values as it is presented in Table 4.
Detection of damage under successful use of exploit based on basic and infrastructural metric
Let us introduce new index I, which will describe damage to an organization with successful realization of exploit. This index will also be used for vulnerability grouping into a certain transitional model condition in the form of service level. For this purpose it is considered to use three attributes of basic metric (C, I, A) and four attributes of infrastructural metric (CR, IR, AR, CDP), the description is presented in Table 3. Infrastructural metric indexes depend on vulnerability use context specific; include possible damage to confidentiality, integrity and availability in a cut of security requirements and potential concomitant damage of certain model condition. Basic metric indexes describe a value of effect on every certain security component, which subsequently is considered in frames of a certain context of infrastructural indexes. Similarly to index of exploit use frequency, basic metric is used for evaluation of primary damage, which represents vector of confidentiality integrity and availability.
Detection of service levels
Let us represent service levels in the form of condition transition model (Markov process). The first condition represents the absence of damage to confidentiality, integrity and availability and can be described in the form of [0,0; 0,0; 0,0]. The last condition represents maximum damage to confidentiality, integrity and availability taking into account infrastructural metric indexes. Condition [1,0; 1,0; 1,0] is absorbing condition and describes the absence of opportunity to use patch in frames of the model. Thus, the first condition corresponds to complete service level SL0, the last represents the absence of service SLx. All conditions between boundary levels can include complete service list as well as any number of services with lower level or the absence of services depending on the model in question (Trope, Power et al, 2007, Tsaregorodtsev, 2013).
Definition of risk level basing on damage and frequency indexes
For risk level dimension, let us introduce a notion of service level presented in the form of Markov process with continuous time. Service levels depend on project decision and information system’ realization variant functioning on the basis of cloud computing technologies, framework of such information system and application list, in other words on the way of information system’ using.
Firstly, we define a vulnerability list according to public data, for example to official messages about vulnerabilities, databases (NVD) or by launching special scanner (Nessus).
As it was already mentioned, the damage from successful exploit use describes a seriousness of the vulnerability. However, this does not mean that two vulnerabilities leading to the same damage have the similar seriousness level for described environment and lead to commensurate decrease of service maintenance. In this connection, it is necessary to solve the task of vulnerability seriousness level intervals determination with the following determination of service levels for them. As a result, we obtain service level list beginning with level without service presentation and ending at complete service list, described in the form of condition model. Service level we define as not empty list of vulnerabilities having influence level from the same interval.
Secondly, condition transition model is explored, which was received during the first step and is supplemented by transition intensity. The transition intensity defines the opportunity when a transition from one condition to another is possible and with what probability it is possible to be in this condition at a certain time interval t. In the risk level estimation model, every condition refers to the total level of vulnerability list seriousness. Thus, a condition transition model describes different risk levels typical for considered environment at the moment of time t. For definition of transition intensity, it is necessary to consider aggregate frequency of exploit use at the certain time interval.
CONCLUSIONES
To solve the problem of forming an organization’s secure cloud infrastructure, it is proposed to use the method of building a protected hybrid cloud environment. The application of this method will significantly increase the efficiency of IT resources, greatly reduce their costs through diversification of the information flows during their migration to hybrid cloud architecture, ensure compliance with security requirements, determine the sequence of critical data processing and ensure the location of this data between protected cloud environment components.
Suggested approach to information security risk estimation allows conduction of cloud environment security functioning in conditions of considered vulnerability class influence and also an effectiveness of measure and facility complex to withstand these vulnerabilities (Tsaregorodtsev, 2017). On the basis of received estimation an opportunity to choose between different variants of cloud computing environment configuration and choose more appropriate way according to security requirements arises.